The Android OS stack and its vulnerabilities: an empirical study
- Published: 20 February 2019
- Volume 24 , pages 2056–2101, ( 2019 )

Cite this article

- Alejandro Mazuera-Rozo 1 , 2 ,
- Jairo Bautista-Mora 1 ,
- Mario Linares-Vásquez ORCID: orcid.org/0000-0003-0161-2888 1 ,
- Sandra Rueda 1 &
- Gabriele Bavota 2
2024 Accesses
15 Citations
3 Altmetric
Explore all metrics
The wide and rapid adoption of Android-based devices in the last years has motivated the usage of Android apps to support a broad range of daily activities. In that sense, being the most popular mobile platform makes it an attractive target for security attacks. In fact, 1,489 security vulnerabilities have been reported in the last three years (2015-2017) for the Android OS (which is the underlying platform for Android-based devices). While there is a plethora of approaches and tools for detecting malware and security issues in Android apps, few research has been done to identify, categorize, or detect vulnerabilities in the Android OS. In this paper we present the largest study so far aimed at analyzing software vulnerabilities in the Android OS. In particular, we analyzed a total of 1,235 vulnerabilities from four different perspectives: vulnerability types and their evolution, CVSS vectors that describe the vulnerabilities, impacted Android OS layers, and their survivability across the Android OS history. Based on our findings, we propose a list of future actions that could be performed by researchers and practitioners to reduce the number of vulnerabilities in the Android OS as well as their impact and survivability.
This is a preview of subscription content, log in via an institution to check access.
Access this article
Price includes VAT (Russian Federation)
Instant access to the full article PDF.
Rent this article via DeepDyve
Institutional subscriptions
Similar content being viewed by others

Vulnerabilities in Android OS: Challenges and Mitigation Techniques

Unveiling the Security Vulnerabilities in Android Operating System

Android Stack Vulnerabilities: Security Analysis of a Decade
We used the base group attributes because it is the only mandatory group.
https://tinyurl.com/yadtggsr
https://tinyurl.com/y9u5odrv
Meta-analysis is a statistical inference technique aimed at consolidating results from more than one study or experiment.
We found 129 vulnerabilities for the 2017-2 period, but we excluded this semester from the RQ 5 analysis because we do not have complete data for 2017-2.
We were not able to classify the layer affected by 5 vulnerabilities.
Note that there is also an Unclear category because in six cases we were not able to identify the type of change because of the patches complexity . For instance, in CVE-2016-3751 several changes were done over 207 files, thus it was not easy to categorize the changes.
https://tinyurl.com/y777kx6s
https://tinyurl.com/yblfv22p
https://tinyurl.com/yaehg5b2
https://tinyurl.com/ya8rbl7n
https://tinyurl.com/ychpav57
https://tinyurl.com/y6v7me9z
For the base group attributes in CVSS 2.0, there are 729 possible combinations of attribute values. Therefore, the 1,235 analyzed vulnerabilities cover 6.72% (49 out of 729) of all the CVSS 2.0 vectors for the base group attributes.
Compared to Linares-Vásquez et al. ( 2017 ), in our dataset we observed 354 new vulnerabilities in the Kernel that have been reported from November 2016 to August 2017.
Note that we only report numbers for vulnerabilities in the AOSP apps and reported as vulnerabilities in the NVD database.
Note that all p -values equal 1.0 after the holm correction procedure. Before that they were in any case all higher than 0.7.
Aosp commit cf1581c66c2ad8c5b1aaca2e43e350cf5974f46d (2017a) http://tinyurl.com/hxqdp7f
Aosp commit 8ec845c8fe0f03bc57c901bc484541bdd6a7cf80 (2017b) http://tinyurl.com/hvndh7r
Aosp commit edd4a76eb4747bd19ed122df46fa46b452c12a0d (2017c) http://tinyurl.com/hkw399d
Ahmad W, Kästner C, Sunshine J, Aldrich J (2016) Inter-app communication in android: Developer challenges. In: Proceedings of the 13th international conference on mining software repositories, MSR ’16. ACM, New York, pp 177–188. https://doi.org/10.1145/2901739.2901762
Anderson B, et al. (2016) Hpe security research. cyber risk report 2016. Tech. rep., Hewlett Packard
Armis (2017) The attack vector “blueborne” exposes almost every connected device. https://www.armis.com/blueborne/
Arzt S, Rasthofer S, Fritz C, Bodden E, Bartel A, Klein J, Le Traon Y, Octeau D, McDaniel P (2014) Flowdroid: Precise context, flow, field, object-sensitive and lifecycle-aware taint analysis for android apps. In: Proceedings of the 35th ACM SIGPLAN Conference on Programming Language Design and Implementation, PLDI ’14. ACM, New York, pp 259–269. https://doi.org/10.1145/2594291.2594299
Avdiienko V, Kuznetsov K, Gorla A, Zeller A, Arzt S, Rasthofer S, Bodden E (2015) Mining apps for abnormal usage of sensitive data. In: ICSE’15, pp 426–436. http://dl.acm.org/citation.cfm?id=2818754.2818808
Backes M, Bugiel S, Derr E (2016) Reliable third-party library detection in android and its security applications. In: Proceedings of the 2016 ACM SIGSAC conference on computer and communications security, CCS ’16. ACM, New York, pp 356–367. https://doi.org/10.1145/2976749.2978333
Bagheri H, Kang E, Malek S, Jackson D (In Press) A formal approach for detection of security flaws in the android permission system. Springer Journal on Formal Aspects of Computing
Bagheri H, Sadeghi A, Garcia J, Malek S (2015) Covert: compositional analysis of android inter-app permission leakage. IEEE Trans Softw Eng 41(9):866–886. https://doi.org/10.1109/TSE.2015.2419611
Article Google Scholar
Beres D (2015) ‘cowboy adventure’ game infects up to 1 million android users with malware. http://www.huffingtonpost.com/2015/07/10/android-security_n_7765842.html
Bhosale A (2014) Precise static analysis of taint flow for android application sets. Master’s thesis, Heinz College Carnegie Mellon University
Brady P (2008) Anatomy & physiology of an android. https://sites.google.com/site/io/anatomy--physiology-of-an-android https://sites.google.com/site/io/anatomy--physiology-of-an-android
Burgess M (2016) Millions of android devices vulnerable to new stagefright exploit. http://www.wired.co.uk/article/stagefright-android-real-world-hack
Cao C, Gao N, Liu P, Xiang J (2015) Towards analyzing the input validation vulnerabilities associated with android system services. In: Proceedings of the 31st annual computer security applications conference, ACSAC 2015. ACM, New York, pp 361–370. https://doi.org/10.1145/2818000.2818033
Castellanos JH, Wuchner T, Ochoa M, Rueda S (2016) Q-floid: Android malware detection with quantitative data flow graphs. In: Singapore cyber-security conference (SG-CRC). IOS Press, pp 13–26
Christensen R (2011) Plane Answers to Complex Questions: The Theory of Linear models, 4th edn. Springer Texts in Statistics Springer, Berlin
Book MATH Google Scholar
Conover WJ (1998) Practical Nonparametric Statistics, 3rd edn. Wiley, New York
Google Scholar
Corporation M (2017) Cve common vulnerabilities and exposures. http://cve.mitre.org
Cumming G (2011) Introduction to the new Statistics: Effect sizes, confidence intervals, and Meta-Analysis. Routledge, Evanston
Cve-2012-6636 (2017) https://www.cvedetails.com/cve/cve-2012-6636
Dimjaševic M, Atzeni S, Ugrina I, Rakamaric Z (2015) Android malware detection based on system calls
Drake JJ, Lanier Z, Mulliner C, Fora PO, Ridley SA, Wicherski G (2014) Android hacker’s handbook. Wiley, New York
Enck W, Gilbert P, Chun BG, Cox L, Jung J, McDaniel P, Sheth AN (2010) Taintdroid: an information-flow tracking system for realtime privacy monitoring on smartphones. In: Proceedings of the 9th USENIX conference on operating systems design and implementation, OSDI’10. USENIX Association, Berkeley, pp 393–407. http://dl.acm.org/citation.cfm?id=1924943.1924971
Enck W, Ongtang M, McDaniel P (2009) On lightweight mobile phone application certification. In: Proceedings of the 16th ACM conference on computer and communications security, CCS ’09. ACM, New York, pp 235–245. https://doi.org/10.1145/1653662.1653691
Fahl S, Harbach M, Muders T, Baumgärtner L., Freisleben B, Smith M (2012) Why eve and mallory love android: an analysis of android ssl (in)security. In: Proceedings of the 2012 ACM conference on computer and communications security, CCS ’12. ACM, New York, pp 50–61. https://doi.org/10.1145/2382196.2382205
Fattori A, Tam K, Khan SJ, Cavallaro L, Reina A (2014) CopperDroid: On the Reconstruction of Android Malware Behaviors. Tech. rep. Royal Holloway University of London
FIRST Organization (2019) Common vulnerability scoring system sig. https://www.first.org/cvss
for Standardization IO (2011) Iso 27005 information security risk management
Garcia J, Hammad M, Ghorbani N, Malek S (2017) Automatic generation of inter-component communication exploits for android applications. In: Proceedings of the 2017 11th joint meeting on foundations of software engineering, ESEC/FSE 2017. ACM, New York, pp 661–671. https://doi.org/10.1145/3106237.3106286
Gasior W, Yang L (2012) Exploring covert channel in android platform. In: 2012 international conference on cyber security, pp 173–177. https://doi.org/10.1109/CyberSecurity.2012.29
Ghafari M, Gadient P, Nierstrasz O (2017) Security smells in android. In: 2017 IEEE 17th international working conference on source code analysis and manipulation (SCAM), pp 121–130. https://doi.org/10.1109/SCAM.2017.24
Gilbert P, Chun BG, Cox LP, Jung J (2011) Vision: automated security validation of mobile apps at app markets. In: Proceedings of the second international workshop on mobile cloud computing and services, MCS ’11. ACM, New York, pp 21–26. https://doi.org/10.1145/1999732.1999740
Gorla A, Tavecchia I, Gross F, Zeller A (2014) Checking app behavior against app descriptions. In: ICSE’14, pp 1025–1035. https://doi.org/10.1145/2568225.2568276
Google (2016) Android security 2015 year in review. https://static.googleusercontent.com/media/source.android.com/en//security/reports/Google_Android_Security_2015_Report_Final.pdf
Google (2017a) Android security bulletins. https://source.android.com/security/bulletin/
Google (2017b) Platform architecture. https://developer.android.com/guide/platform/index.html
Graf J, Hecker MMM (2015) Jodroid: Adding android support to a static information flow control tool. In: Working conference on programming languages
Grissom RJ, Kim JJ (2005) Effect sizes for research: a broad practical approach, 2nd edn. Lawrence Earlbaum Associates, New Jersey
Hedges LV, Olkin I (1985) Statistical methods for Meta-Analysis. Academic Press, New York
MATH Google Scholar
Herzig K, Zeller A (2013) The impact of tangled code changes. In: Proceedings of the 10th Working Conference on Mining Software Repositories, MSR ’13, San Francisco, pp 121–130
Holm S (1979) A simple sequentially rejective Bonferroni test procedure. Scand J Stat 6:65–70
Huang H, Zhu S, Chen K, Liu P (2015) From system services freezing to system server shutdown in android: All you need is a loop in an app. In: Proceedings of the 22nd ACM SIGSAC conference on computer and communications security, CCS ’15. ACM, New York, pp 1236–1247. https://doi.org/10.1145/2810103.2813606
Jimenez M, Papadakis M, Bissyandé TF, Klein J (2016) Profiling android vulnerabilities. In: 2016 IEEE International conference on software quality, reliability and security (QRS), pp 222–229. https://doi.org/10.1109/QRS.2016.34 https://doi.org/10.1109/QRS.2016.34
Kantola D, Chin E, He W, Wagner D (2012) Reducing attack surfaces for intra-application communication in android. In: Proceedings of the second ACM workshop on security and privacy in smartphones and mobile devices, SPSM ’12. ACM, New York, pp 69–80. https://doi.org/10.1145/2381934.2381948
Kim S, James Whitehead Jr E, Zhang Y (2008) Classifying software changes: clean or buggy? IEEE Trans Softw Eng 34(2):181–196
Lal S, Sureka A (2012) Comparison of seven bug report types: a case-study of google chrome browser project. In: 2012 19th asia-pacific software engineering conference, vol 1, pp 517–526. https://doi.org/10.1109/APSEC.2012.54
Lee S, Hwang S, Ryu S (2017) All about activity injection: Threats, semantics, and detection. In: Proceedings of the 32nd IEEE/ACM international conference on automated software engineering, ASE 2017. IEEE Press, Piscataway, pp 252–262. http://dl.acm.org/citation.cfm?id=3155562.3155597
Li GK (2010) Computing inter-rater reliability and its variance in the presence of high agreement. Br J Math Stat Psychol 61(1):29–48. https://doi.org/10.1348/000711006X126600
MathSciNet Google Scholar
Linares-Vásquez M, Bavota G, Escobar-Velásquez C (2017) An empirical study on android-related vulnerabilities. In: Proceedings of the 14th international conference on mining software repositories, MSR ’17. IEEE Press, Piscataway, pp 2–13. https://doi.org/10.1109/MSR.2017.60
LLC PI (2014) The security impact of mobile device use by employees. Tech. rep., Ponemon Institute
Lu L, Li Z, Wu Z, Lee W, Jiang G (2012) Chex: statically vetting android apps for component hijacking vulnerabilities. In: ACM Conference on computer and communications security, pp 229–240
Mazuera-Rozo A, Bautista-Mora J, Linares-Vásquez M, Rueda S, Bavota G (2017) Replication package: “The Android OS Stack and its Vulnerabilities: An Empirical Study”. http://ml-papers.gitlab.io/android.vulnerabilities-2017/appendix/
Mell P, Scarfone K, Romanosky S (2007) A Complete Guide to the Common Vulnerability Scoring System Version 2.0, 2.0 edn
MITRE (2017a) Cwe-120: Buffer copy without checking size of input (‘classic buffer overflow’). https://cwe.mitre.org/data/definitions/120.html
MITRE (2017b) Cwe-121: Stack-based buffer overflow. https://cwe.mitre.org/data/definitions/121.html
MITRE (2017c) Cwe-122: Heap-based buffer overflow. https://cwe.mitre.org/data/definitions/122.html
MITRE (2017d) Cwe-190: Integer overflow or wraparound. https://cwe.mitre.org/data/definitions/190.html
MITRE (2017e) Cwe-201: Information exposure through sent data. https://cwe.mitre.org/data/definitions/201.html
MITRE (2017f) Cwe-275: Permission issues. https://cwe.mitre.org/data/definitions/275.html
MITRE (2017g) Cwe-296: Improper following of a certificate’s chain of trust. https://cwe.mitre.org/data/definitions/296.html
MITRE (2017h) Cwe-326: Inadequate encryption strength. https://cwe.mitre.org/data/definitions/326.html
MITRE (2017i) Cwe-327: Use of a broken or risky cryptographic algorithm. https://cwe.mitre.org/data/definitions/327.html
MITRE (2017j) Cwe-415: Double free. https://cwe.mitre.org/data/definitions/415.html
MITRE (2017k) Cwe-787: Out-of-bounds write. https://cwe.mitre.org/data/definitions/787.html
MITRE (2017l) Cwe-840: Business logic errors. https://cwe.mitre.org/data/definitions/840.html
MITRE (2017m) Cwe-862: Missing authorization. https://cwe.mitre.org/data/definitions/862.html
MITRE (2017n) Cwe-909: Missing initialization of resource. https://cwe.mitre.org/data/definitions/909.html
MITRE (2017o) Cwe-94: Improper control of generation of code (’code injection’). https://cwe.mitre.org/data/definitions/94.html
MITRE (2017p) Common weakness enumeration http://cwe.mitre.org/
MITRE (2017q) Cve details Android vulnerabilities. https://www.cvedetails.com/product/19997/Google-Android.html
MITRE (2017r) Cve details. https://www.cvedetails.com/
Morales LV, Rueda SJ (2015) Meaningful permission management in android. IEEE Lat Am Trans 13(4):1160–1166. https://doi.org/10.1109/TLA.2015.7106371
Nickinson P (2015) The ’stagefright’ exploit: what you need to know. http://www.androidcentral.com/stagefright
NIST (2015) Common vulnerability scoring system calculator version 2. https://nvd.nist.gov/vuln-metrics/cvss/v2-calculator
NIST (2017) Nvd data feeds http://nvd.nist.gov/download.cfm#{RSS}
Novak E, Tang Y, Hao Z, Li Q, Zhang Y (2015) Physical media covert channels on smart mobile devices. In: Proceedings of the 2015 ACM international joint conference on pervasive and ubiquitous computing, UbiComp ’15. ACM, New York, pp 367–378. https://doi.org/10.1145/2750858.2804253
Park Y, Reeves DS (2013) Deriving common malware behavior through graph clustering. Comput Secur 39(PART B):419–430. https://doi.org/10.1016/j.cose.2013.09.006
Ren C, Zhang Y, Xue H, Wei T, Liu P (2015) Towards discovering and understanding task hijacking in android. In: Proceedings of the 24th USENIX conference on security symposium, SEC’15. USENIX Association, Berkeley, pp 945–959. http://dl.acm.org/citation.cfm?id=2831143.2831203
Rust (2013) https://www.rust-lang.org
Sadeghi A, Bagheri H, Malek S (2015) Analysis of android inter-app security vulnerabilities using covert. In: ICSE’15, pp 725–728. http://dl.acm.org/citation.cfm?id=2819009.2819149
Sadeghi A, Bagheri H, Garcia J, Malek S (2016) A taxonomy and qualitative comparison of program analysis techniques for security assessment of android software. IEEE Trans Softw Eng PP(99):1–1. https://doi.org/10.1109/TSE.2016.2615307
Sadeghi A, Jabbarvand R, Malek S (2017) Patdroid: Permission-aware gui testing of android. In: Proceedings of the 2017 11th joint meeting on foundations of software engineering, ESEC/FSE 2017. ACM, New York, pp 220–232. https://doi.org/10.1145/3106237.3106250
Sbîrlea D, Burke MG, Guarnieri S, Pistoia M, Sarkar V (2013) Automatic detection of inter-application permission leaks in android applications. IBM J Res Dev 57(6):2:10–2:10. https://doi.org/10.1147/JRD.2013.2284403 https://doi.org/10.1147/JRD.2013.2284403
Sliwerski J, Zimmermann T, Zeller A (2005) When do changes induce fixes? In: Proceedings of the 2005 International Workshop on Mining Software Repositories
Stefanko L (2015) Aggressive android ransomware spreading in the usa. http://www.welivesecurity.com/2015/09/10/aggressive-android-ransomware-spreading-in-the-usa/
Sufatrio Tan DJJ, Chua TW, Thing VLL (2015) Securing android: a survey, taxonomy, and challenges. ACM Comput Surv 47(4):58:1–58:45. https://doi.org/10.1145/2733306
Thomas DR (2015a) The Lifetime of Android API Vulnerabilities: Case Study on the JavaScript-to-Java Interface (Transcript of Discussion). Springer International Publishing, Cham, pp 139–144. https://doi.org/10.1007/978-3-319-26096-9_14
Thomas DR, Beresford AR, Rice A (2015b) Security metrics for the android ecosystem. In: Proceedings of the 5th annual ACM CCS workshop on security and privacy in smartphones and mobile devices, SPSM ’15. ACM, New York, pp 87–98. https://doi.org/10.1145/2808117.2808118
Tufano M, Watson C, Bavota G, Di Penta M, White M, Poshyvanyk D (2018) An empirical investigation into learning bug-fixing patches in the wild via neural machine translation. In: Proceedings of the 33rd ACM/IEEE international conference on automated software engineering, ASE 2018. ACM, New York, pp 832–837. https://doi.org/10.1145/3238147.3240732
U.S. National Institute of Standards and Technology - NIST (2012) National vulnerability database. http://nvd.nist.gov
U.S. National Institute of Standards and Technology - NIST (2012) Sp 800-30 guide for conducting risk assessments
VisionMobile: Developer economics q1 2014 (2014) State of the developer nation. Tech. rep.
Wang K, Zhang Y, Liu P (2016) Call me back!: Attacks on system server and system apps in android through synchronous callback. In: Proceedings of the 2016 ACM SIGSAC conference on computer and communications security, CCS ’16. ACM, New York, pp 92–103. https://doi.org/10.1145/2976749.2978342
Weichselbaum L, Neugschwandtner M, Lindorfer M, Fratantonio Y, Veen VVD, Platzer C (2012) ANDRUBIS: Android Malware Under The Magnifying Glass. Tech. rep., Vienna University of Technology. https://www.iseclab.org/papers/andrubis_techreport.pdf
wiki. L (2015) Android kernel features. http://elinux.org/Android_Kernel_Features
Wikipedia (2017a) Android version history https://en.wikipedia.org/wiki/Android_version_history
Wikipedia (2017b) Heartbleed https://en.wikipedia.org/wiki/Heartbleed
Wikipedia (2017c) Stagefright https://en.wikipedia.org/wiki/Stagefright_(bug)
Wu L, Grace M, Zhou Y, Wu C, Jiang X (2013) The impact of vendor customizations on android security. In: Proceedings of the 2013 ACM SIGSAC conference on computer & communications security, CCS ’13. ACM, New York, pp 623–634. https://doi.org/10.1145/2508859.2516728
Xiao X, Tillman N, Fahndrich M, DeHalleux J, Moskal M (2012) User-aware privacy control via extended static-information-flow analysis. In: IEEE/ACM international conference on automated software engineering
Xu M, Song C, Ji Y, Shih MW, Lu K, Zheng C, Duan R, Jang Y, Lee B, Qian C, Lee S, Kim T (2016) Toward engineering a secure android ecosystem: a survey of existing techniques. ACM Comput Surv 49(2):38:1–38:47. https://doi.org/10.1145/2963145
You W, Liang B, Shi W, Zhu S, Wang P, Xie S, Zhang X (2016) Reference hijacking: Patching, protecting and analyzing on unmodified and non-rooted android devices. In: Proceedings of the 38th international conference on software engineering, ICSE ’16. ACM, New York, pp 959–970. https://doi.org/10.1145/2884781.2884863
Zaman S, Adams B, Hassan AE (2011) Security versus performance bugs: a case study on firefox. In: Proceedings of the 8th working conference on mining software repositories, MSR’11. ACM, New York, pp 93–102. https://doi.org/10.1145/1985441.1985457
Zhou Y, Jiang X (2012) Android malware genome project. http://www.malgenomeproject.org/
Zhou Y, Jiang X (2012) Dissecting android malware: characterization and evolution. In: 2012 IEEE Symposium on security and privacy, pp 95–109. https://doi.org/10.1109/SP.2012.16
Zuo C, Wu J, Guo S (2015) Automatically detecting ssl error-handling vulnerabilities in hybrid mobile web apps. In: Proceedings of the 10th ACM symposium on information, computer and communications security, ASIA CCS ’15. ACM, New York, pp 591–596. https://doi.org/10.1145/2714576.2714583
Download references
Author information
Authors and affiliations.
Universidad de los Andes, Bogotá, Colombia
Alejandro Mazuera-Rozo, Jairo Bautista-Mora, Mario Linares-Vásquez & Sandra Rueda
Università della Svizzera italiana, Lugano, Switzerland
Alejandro Mazuera-Rozo & Gabriele Bavota
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Mario Linares-Vásquez .
Additional information
Communicated by: Lin Tan
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Reprints and permissions
About this article
Mazuera-Rozo, A., Bautista-Mora, J., Linares-Vásquez, M. et al. The Android OS stack and its vulnerabilities: an empirical study. Empir Software Eng 24 , 2056–2101 (2019). https://doi.org/10.1007/s10664-019-09689-7
Download citation
Published : 20 February 2019
Issue Date : 15 August 2019
DOI : https://doi.org/10.1007/s10664-019-09689-7
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Vulnerabilities
- Empirical study
- Operating system
- Find a journal
- Publish with us
- Track your research
Help | Advanced Search
Computer Science > Operating Systems
Title: android os case study.
Abstract: Android is a mobile operating system based on a modified version of the Linux kernel and other open source software, designed primarily for touchscreen mobile devices such as smartphones and tablets. It is an operating system for low powered devices that run on battery and are full of hardware like Global Positioning System (GPS) receivers, cameras, light and orientation sensors, Wi-Fi and LTE (4G telephony) connectivity and a touch screen. Like all operating systems, Android enables applications to make use of the hardware features through abstraction and provide a defined environment for applications. The study includes following topic: Background And History Android Architecture Kernel And StartUp Process Process Management Deadlock CPU Scheduling Memory Management Storage Management I/O Battery Optimization
Submission history
Access paper:.
- Other Formats
References & Citations
- Google Scholar
- Semantic Scholar
DBLP - CS Bibliography
Bibtex formatted citation.
Bibliographic and Citation Tools
Code, data and media associated with this article, recommenders and search tools.
- Institution
arXivLabs: experimental projects with community collaborators
arXivLabs is a framework that allows collaborators to develop and share new arXiv features directly on our website.
Both individuals and organizations that work with arXivLabs have embraced and accepted our values of openness, community, excellence, and user data privacy. arXiv is committed to these values and only works with partners that adhere to them.
Have an idea for a project that will add value for arXiv's community? Learn more about arXivLabs .
A Review of Android and iOS Operating System Security
Ieee account.
- Change Username/Password
- Update Address
Purchase Details
- Payment Options
- Order History
- View Purchased Documents
Profile Information
- Communications Preferences
- Profession and Education
- Technical Interests
- US & Canada: +1 800 678 4333
- Worldwide: +1 732 981 0060
- Contact & Support
- About IEEE Xplore
- Accessibility
- Terms of Use
- Nondiscrimination Policy
- Privacy & Opting Out of Cookies
A not-for-profit organization, IEEE is the world's largest technical professional organization dedicated to advancing technology for the benefit of humanity. © Copyright 2024 IEEE - All rights reserved. Use of this web site signifies your agreement to the terms and conditions.
Accessibility Links
- Skip to content
- Skip to search IOPscience
- Skip to Journals list
- Accessibility help
- Accessibility Help
Click here to close this panel.
Purpose-led Publishing is a coalition of three not-for-profit publishers in the field of physical sciences: AIP Publishing, the American Physical Society and IOP Publishing.
Together, as publishers that will always put purpose above profit, we have defined a set of industry standards that underpin high-quality, ethical scholarly communications.
We are proudly declaring that science is our only shareholder.
Design and Development of Android Application for Educational Institutes
Chukwuebuka Joseph Ejiyi 1 , Jianhua Deng 1 , Thomas Ugochukwu Ejiyi 2 , Adetunji A Salako 3 , Makuachukwu B Ejiyi 4 and Chinonso G Anomihe 5
Published under licence by IOP Publishing Ltd Journal of Physics: Conference Series , Volume 1769 , 5th International Conference on Computer Science and Information Engineering (ICCSIE 2020) 23-25 October 2020, Dalian, China Citation Chukwuebuka Joseph Ejiyi et al 2021 J. Phys.: Conf. Ser. 1769 012066 DOI 10.1088/1742-6596/1769/1/012066
Article metrics
1377 Total downloads
Share this article
Author e-mails.
Author affiliations
1 School of Information and Software Engineering, University of Electronic Science and Technology of China, Chengdu, PRC
2 Department of Pure and Industrial Chemistry, University of Nigeria Nsukka, Enugu State, Nigeria
3 School of Computer Science and Engineering, University of Electronic Science and Technology of China, Chengdu, PRC
4 Department of Agricultural Extensions, University of Nigeria Nsukka, Enugu State, Nigeria
5 Department of Biochemistry, Federal University of Technology Owerri, Imo State, Nigeria
Buy this article in print
The growth in the use android applications (Apps) has made it the most popular smart device operating system in use nowadays. Android has over 76% of the mobile operating system from December 2018–January 2020 which is quite significant. Android phones are also becoming the most used electronics globally. Students of higher institutions of learning are also becoming accustomed to the use of applications such that they want everything available for them on their mobile device if possible. This paper deals on an android application that will aid students in planning their timetable and scheduling their classes as well as having full knowledge of days according to the school calendar, get access to academic resources and information about the school right on their smart devices. From the application, one can have access to the detailed and accurate information of the school.
Export citation and abstract BibTeX RIS
Content from this work may be used under the terms of the Creative Commons Attribution 3.0 licence . Any further distribution of this work must maintain attribution to the author(s) and the title of the work, journal citation and DOI.
Subscribe to the PwC Newsletter
Join the community, edit social preview.

Add a new code entry for this paper
Remove a code repository from this paper, mark the official implementation from paper authors, add a new evaluation result row, remove a task, add a method, remove a method, edit datasets, android os case study.
19 Apr 2021 · Mayank Goel , Gourav Singal · Edit social preview
Android is a mobile operating system based on a modified version of the Linux kernel and other open source software, designed primarily for touchscreen mobile devices such as smartphones and tablets. It is an operating system for low powered devices that run on battery and are full of hardware like Global Positioning System (GPS) receivers, cameras, light and orientation sensors, Wi-Fi and LTE (4G telephony) connectivity and a touch screen. Like all operating systems, Android enables applications to make use of the hardware features through abstraction and provide a defined environment for applications. The study includes following topic: Background And History Android Architecture Kernel And StartUp Process Process Management Deadlock CPU Scheduling Memory Management Storage Management I/O Battery Optimization
Code Edit Add Remove Mark official
Datasets edit.
- Enabling Opportunity

Dig deeper with in‑depth resources, white papers, case studies, and surveys.
The android ecosystem, you say you want a mobile revolution….
Google CEO Sundar Pichai shares how Android is changing the ways people use mobile devices.
Android fuels innovation and choice
Discover how Android offers more choice and freedom to manufacturers, developers, and consumers.
Four myths about Android
ZDNet looks into common myths about Android and sets the record straight.
Economic impact
Google is a growth engine for europe.
Discover all the ways Google is helping dozens of European businesses grow online
Mobile tech drives the EU economy
See how the development of mobile devices and software contributes £73bn to the EU economy.
For the next five billion: Android One
The Android One initiative is helping people across the globe access affordable mobile devices.
Breaking the $100 barrier
See how Google teamed up with device maker Infinix to sell Android phones in Africa for less than $100.
Launching Android One in Africa
By partnering with regional players, Google has helped get low-cost phones to developing countries.
The growing mobile Internet economy
Explore the impact of mobile technology in the 13 countries that make up about 70 percent of global GDP.
Embracing innovation
How emerging markets fuel disruption.
Discover why markets like China, Vietnam and India are primed to disrupt the global mobile industry.
Keep Android harmonized
The president of the App Developers Alliance argues against further fragmentation of the Android ecosystem.
Let’s talk about Android
Discover the impact of Android’s open-source model on competition in the field of mobile operating systems.
Explore these carousel items. Use the previous and next buttons, as well as the keyboard arrows, to change the displayed item.
Suggestions or feedback?
MIT News | Massachusetts Institute of Technology
- Machine learning
- Social justice
- Black holes
- Classes and programs
Departments
- Aeronautics and Astronautics
- Brain and Cognitive Sciences
- Architecture
- Political Science
- Mechanical Engineering
Centers, Labs, & Programs
- Abdul Latif Jameel Poverty Action Lab (J-PAL)
- Picower Institute for Learning and Memory
- Lincoln Laboratory
- School of Architecture + Planning
- School of Engineering
- School of Humanities, Arts, and Social Sciences
- Sloan School of Management
- School of Science
- MIT Schwarzman College of Computing
Using ideas from game theory to improve the reliability of language models
Press contact :.

Previous image Next image
Imagine you and a friend are playing a game where your goal is to communicate secret messages to each other using only cryptic sentences. Your friend's job is to guess the secret message behind your sentences. Sometimes, you give clues directly, and other times, your friend has to guess the message by asking yes-or-no questions about the clues you've given. The challenge is that both of you want to make sure you're understanding each other correctly and agreeing on the secret message.
MIT Computer Science and Artificial Intelligence Laboratory (CSAIL) researchers have created a similar "game" to help improve how AI understands and generates text. It is known as a “consensus game” and it involves two parts of an AI system — one part tries to generate sentences (like giving clues), and the other part tries to understand and evaluate those sentences (like guessing the secret message).
The researchers discovered that by treating this interaction as a game, where both parts of the AI work together under specific rules to agree on the right message, they could significantly improve the AI's ability to give correct and coherent answers to questions. They tested this new game-like approach on a variety of tasks, such as reading comprehension, solving math problems, and carrying on conversations, and found that it helped the AI perform better across the board.
Traditionally, large language models answer one of two ways: generating answers directly from the model (generative querying) or using the model to score a set of predefined answers (discriminative querying), which can lead to differing and sometimes incompatible results. With the generative approach, "Who is the president of the United States?" might yield a straightforward answer like "Joe Biden." However, a discriminative query could incorrectly dispute this fact when evaluating the same answer, such as "Barack Obama."
So, how do we reconcile mutually incompatible scoring procedures to achieve coherent, efficient predictions?
"Imagine a new way to help language models understand and generate text, like a game. We've developed a training-free, game-theoretic method that treats the whole process as a complex game of clues and signals, where a generator tries to send the right message to a discriminator using natural language. Instead of chess pieces, they're using words and sentences," says Athul Jacob, an MIT PhD student in electrical engineering and computer science and CSAIL affiliate. "Our way to navigate this game is finding the 'approximate equilibria,' leading to a new decoding algorithm called 'equilibrium ranking.' It's a pretty exciting demonstration of how bringing game-theoretic strategies into the mix can tackle some big challenges in making language models more reliable and consistent."
When tested across many tasks, like reading comprehension, commonsense reasoning, math problem-solving, and dialogue, the team's algorithm consistently improved how well these models performed. Using the ER algorithm with the LLaMA-7B model even outshone the results from much larger models. "Given that they are already competitive, that people have been working on it for a while, but the level of improvements we saw being able to outperform a model that's 10 times the size was a pleasant surprise," says Jacob.
"Diplomacy," a strategic board game set in pre-World War I Europe, where players negotiate alliances, betray friends, and conquer territories without the use of dice — relying purely on skill, strategy, and interpersonal manipulation — recently had a second coming. In November 2022, computer scientists, including Jacob, developed “Cicero,” an AI agent that achieves human-level capabilities in the mixed-motive seven-player game, which requires the same aforementioned skills, but with natural language. The math behind this partially inspired the Consensus Game.
While the history of AI agents long predates when OpenAI's software entered the chat in November 2022, it's well documented that they can still cosplay as your well-meaning, yet pathological friend.
The consensus game system reaches equilibrium as an agreement, ensuring accuracy and fidelity to the model's original insights. To achieve this, the method iteratively adjusts the interactions between the generative and discriminative components until they reach a consensus on an answer that accurately reflects reality and aligns with their initial beliefs. This approach effectively bridges the gap between the two querying methods.
In practice, implementing the consensus game approach to language model querying, especially for question-answering tasks, does involve significant computational challenges. For example, when using datasets like MMLU, which have thousands of questions and multiple-choice answers, the model must apply the mechanism to each query. Then, it must reach a consensus between the generative and discriminative components for every question and its possible answers.
The system did struggle with a grade school right of passage: math word problems. It couldn't generate wrong answers, which is a critical component of understanding the process of coming up with the right one.
“The last few years have seen really impressive progress in both strategic decision-making and language generation from AI systems, but we’re just starting to figure out how to put the two together. Equilibrium ranking is a first step in this direction, but I think there’s a lot we’ll be able to do to scale this up to more complex problems,” says Jacob.
An avenue of future work involves enhancing the base model by integrating the outputs of the current method. This is particularly promising since it can yield more factual and consistent answers across various tasks, including factuality and open-ended generation. The potential for such a method to significantly improve the base model's performance is high, which could result in more reliable and factual outputs from ChatGPT and similar language models that people use daily.
"Even though modern language models, such as ChatGPT and Gemini, have led to solving various tasks through chat interfaces, the statistical decoding process that generates a response from such models has remained unchanged for decades," says Google Research Scientist Ahmad Beirami, who was not involved in the work. "The proposal by the MIT researchers is an innovative game-theoretic framework for decoding from language models through solving the equilibrium of a consensus game. The significant performance gains reported in the research paper are promising, opening the door to a potential paradigm shift in language model decoding that may fuel a flurry of new applications."
Jacob wrote the paper with MIT-IBM Watson Lab researcher Yikang Shen and MIT Department of Electrical Engineering and Computer Science assistant professors Gabriele Farina and Jacob Andreas, who is also a CSAIL member. They presented their work at the International Conference on Learning Representations (ICLR) earlier this month, where it was highlighted as a "spotlight paper." The research also received a “best paper award” at the NeurIPS R0-FoMo Workshop in December 2023.
Share this news article on:
Press mentions, quanta magazine.
MIT researchers have developed a new procedure that uses game theory to improve the accuracy and consistency of large language models (LLMs), reports Steve Nadis for Quanta Magazine . “The new work, which uses games to improve AI, stands in contrast to past approaches, which measured an AI program’s success via its mastery of games,” explains Nadis.
Previous item Next item
Related Links
- Article: "Game Theory Can Make AI More Correct and Efficient"
- Jacob Andreas
- Athul Paul Jacob
- Language & Intelligence @ MIT
- Computer Science and Artificial Intelligence Laboratory (CSAIL)
- Department of Electrical Engineering and Computer Science
- MIT-IBM Watson AI Lab
Related Topics
- Computer science and technology
- Artificial intelligence
- Human-computer interaction
- Natural language processing
- Game theory
- Electrical Engineering & Computer Science (eecs)
Related Articles

Reasoning and reliability in AI

Explained: Generative AI

Synthetic imagery sets new bar in AI training efficiency

Simulating discrimination in virtual reality
More mit news.

H2 underground
Read full story →

2024 MAD Design Fellows announced

School of Engineering first quarter 2024 awards

From NASA to MIT to Formlabs

An expansive approach to making new compounds

Q&A: A graduating student looks back on his MIT experience
- More news on MIT News homepage →
Massachusetts Institute of Technology 77 Massachusetts Avenue, Cambridge, MA, USA
- Map (opens in new window)
- Events (opens in new window)
- People (opens in new window)
- Careers (opens in new window)
- Accessibility
- Social Media Hub
- MIT on Facebook
- MIT on YouTube
- MIT on Instagram

IMAGES
VIDEO
COMMENTS
Research-Paper- 1068648.html [5] ... This paper is about Android as open source operating system and why various smartphone manufactures considered it as their main operating system.
Android is one of the mobile operating systems based on the Linux-Operating System, including a system, applications and middleware which developed by Google. Android provides platform for ...
A. INTRODUCTION: Android Operating is primarily de signed for touchscreen. devices like mobile, tablet and smartphone. Android OS is. based on a Linux kernel and other open-sou rce software. We ...
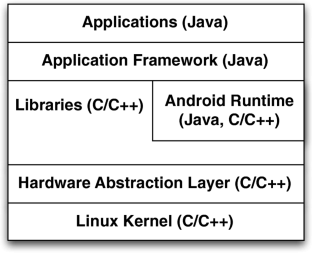
The Android operating unit is a mobile phone operating body built through Google primarily for touchscreen tools, smartphones, and tablet computers. It will undoubtedly begin with Android Architecture, which consists of five degrees: the Linux piece, Libraries, Application structure, Android runtime, and System apps.
This research paper focuses on some recent and most popular security vulnerabilities found in the android mobile operating system. The key contribution of this research includes the identification of mitigation techniques to overcome the challenges faced by its user The security of android devices can be significantly improved If mitigation ...
According to Andy Rubin, one of Android's founders, Android Inc. was to develop "smarter mobile devices that are more aware of its owner's location and preferences.". Rubin further stated, "If people are smart, that information starts getting aggregated into consumer products.". The year was 2003 and the location was Palo Alto ...
Although in the last few years significant research progress is seen in the field of the detection and mitigation of Android security, yet numerous challenges and gaps still exist. This paper presents a comprehensive and sound taxonomy to review the state-of-the-art approaches used in Android security.
The Android platform has become one of the most popular operating system with millions of new users each year and the history including improvements involved in each release as well as the systems architecture and project structure is described. - Due to the technological development, mobile terminals have evolved into functionally sophisticated devices such as smartphones and tablets.
The wide and rapid adoption of Android-based devices in the last years has motivated the usage of Android apps to support a broad range of daily activities. In that sense, being the most popular mobile platform makes it an attractive target for security attacks. In fact, 1,489 security vulnerabilities have been reported in the last three years (2015-2017) for the Android OS (which is the ...
Android is a mobile operating system based on a modified version of the Linux kernel and other open source software, designed primarily for touchscreen mobile devices such as smartphones and tablets. It is an operating system for low powered devices that run on battery and are full of hardware like Global Positioning System (GPS) receivers, cameras, light and orientation sensors, Wi-Fi and LTE ...
In this paper, the Android OS environment, feature selection, classification models, and confronted challenges of machine learning detection are described in detail. ... The correlative research on Android malware collected in this paper can provide valuable reference and broaden the research direction for future researchers.
With the advent of new mobile technologies, the mobile application industry is advancing rapidly. Consisting of several operating systems like symbian OS, iOS, blackberry, etc., Android OS is recognized as the most widely used, popular and user-friendly mobile platform. This open-source linux kernel-based operating system offers high flexibility due to its customization properties making it a ...
The paper concludes by laying down future research directions and scope of work, which can be leveraged not only by application developers, but also by researchers. This will help make Android safer for users and will further increase its demand as a mobile operating system .
is shown in figure 1. The application layer in an android. operating system is the top layer that inc lude utilities like. SMS, contacts, phone, browser, ca mera, media player, cleaner, etc.All of ...
Prior to the invention of smartphones, mobile phones were simply meant for making calls. However, since then, they have developed into low-powered handheld computers. The operating system of mobile phones, which gave them intelligence and independent processing and storage, was the driving force behind this evolution.
Android Operating System: Architecture, Security Challenges and Solutions. March 2016; ... According to review, there is a research paper on security issues on android smart phones. Paper is
Android and iOS are the major operating systems for mobile devices and share over 99% of the mobile device market. This research aims to conduct a comparative analysis of the security of the components in the Android and iOS operating systems. ... From the analysis, it is evident that iOS is more secure than Android operating system. However ...
Finally, the conclusion is provided in Section 9 of the paper. 2. Related work. Research work carried out in the domain of smartphone security deals with issues like vulnerabilities in smartphones, malware impact, security procedures in mobile platforms, and different policies used for safety and privacy of users. ... Android is an open-source ...
Abstract. The growth in the use android applications (Apps) has made it the most popular smart device operating system in use nowadays. Android has over 76% of the mobile operating system from December 2018-January 2020 which is quite significant. Android phones are also becoming the most used electronics globally.
Android OS CASE STUDY. Android is a mobile operating system based on a modified version of the Linux kernel and other open source software, designed primarily for touchscreen mobile devices such as smartphones and tablets. It is an operating system for low powered devices that run on battery and are full of hardware like Global Positioning ...
Let's talk about Android. Discover the impact of Android's open-source model on competition in the field of mobile operating systems. Dig deeper with articles, blog posts, and other resources that reveal how Android is encouraging competition and fueling the global mobile economy.
MySQL for database design and development. Android is an open-source mobile phone operating system based on Linux and developed by Google[2] and now a day it becomes the most widely used Operating System on mobile phones. Java language codes are used to develop android mobile application which allows developers to write codes in the Java
Prior to GPT-4o, you could use Voice Mode to talk to ChatGPT with latencies of 2.8 seconds (GPT-3.5) and 5.4 seconds (GPT-4) on average. To achieve this, Voice Mode is a pipeline of three separate models: one simple model transcribes audio to text, GPT-3.5 or GPT-4 takes in text and outputs text, and a third simple model converts that text back to audio.
MIT researchers' "consensus game" is a game-theoretic approach for language model decoding. The equilibrium-ranking algorithm harmonizes generative and discriminative querying to enhance prediction accuracy across various tasks, outperforming larger models and demonstrating the potential of game theory in improving language model consistency and truthfulness.
features of the OS with various user services. This paper presents a comparative study of six (i.e. Windows, Linux, Mac, UNIX, Android and iOS) operating systems. based on the OS features and ...
Introduction. Android is a mobil e operating system base d on a modified version of the Linux k ernel and. other open source software, designed primarily for touchscre en mobile devices such as ...